MFA on shared accounts

Adding MFA on shared accounts
Some people might be surprised that using MFA (multifactor authentication) on shared accounts is possible. And that, yes, MFA should be used for shared accounts just like it should be used for regular accounts.
Many services allow you to add several second factors. The first option is to leverage this and add a second factor per individual, for example, a separate hardware token or passkey per person. Problem solved. This is a viable option, as it allows you (at least in some cases and with some work) to identify who logged in based on the second factor used.
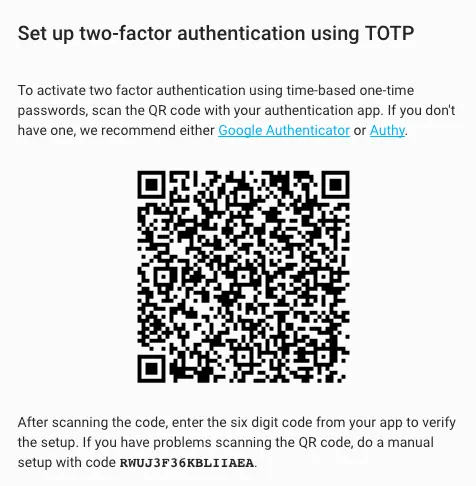
All hope is not lost for service not offering you that option. TOTP-based authentications (typically those that ask you for a six-digit PIN) can also be used. The secret (or the QR code) can be passed on to multiple users. Save the secret safely (in a password manager, for example) and give it to the new staff who need it. Or print the QR code somewhere handy (after considering your threat model).